Current Attack Campaign Leveraging Critical Vulnerabilities Against Cisco ASA & FTD VPN appliances (CVE-2025-20333, CVE-2025-20363)
Executive Summary
On September 25, Cisco published several advisories concerning critical vulnerabilities in their Cisco Adaptive Security Appliance (ASA) and FirePower Threat Defense (FTD) product lines. These vulnerabilities have been actively exploited in the wild since earlier this year by a sophisticated adversary. The malicious activity has been attributed to the 2024 "ArcaneDoor" campaign, with current evidence indicating that the same threat actors involved in previous incidents are responsible for the ongoing attacks.
The threat actor has leveraged these vulnerabilities to deploy stealthy in-memory backdoors and bootkits on certain models of Cisco ASA devices, allowing them to retain persistent access to compromised appliances. Cisco released advisories addressing three critical vulnerabilities involved: CVE-2025-20333, CVE-2025-20362, and CVE-2025-20363. Additionally, Cisco published a detailed report outlining the current attack campaign targeting Cisco ASA devices and provided guidance for detecting malicious activity indicative of potential exploitation. While Cisco FTD devices are impacted by these vulnerabilities, the persistent implants have not yet been observed on those platforms due to the use of Secure Boot technologies.
In response to this attack campaign, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued Emergency Directive ED 25-03, mandating that all U.S. federal agencies analyze their Cisco ASA and Firepower devices for signs of compromise by September 26. Following the release of the directive, CISA distributed a supplemental instruction guide under ED 25-03, which contains specific steps for conducting forensic dumps and threat hunting on affected devices. Several international organizations, including the UK's National Cyber Security Centre and Canada's Centre for Cyber Security, have also released guidance to address this campaign.
All vulnerabilities involved in this ongoing attack campaign result from improper validation of HTTP requests to the Cisco AnyConnect Web UI. Successful exploitation allows remote code execution (RCE) on the targeted device. In particular, CVE-2025-20362 and CVE-2025-20363 have been observed as part of an "exploit chain," enabling unauthenticated attackers to achieve complete compromise of affected appliances. Because Cisco ASA products are internet-facing by design and include VPN functionality, a successful attack on one of these devices can grant an adversary initial access to an organization's internal network.
Given the ongoing exploitation of these vulnerabilities and the potential risks posed by compromised edge devices, Beazley Security strongly recommends organizations using affected systems to apply available patches immediately. Organizations should also leverage the detection guidance provided in this document to assess whether they have been impacted by post-exploitation implants.
Additionally, Beazley Security is aware of a notable increase internet scan traffic attempting to identify exposed Cisco ASA and FTD devices. This trend may suggest that other threat actors are actively seeking to exploit these vulnerabilities beyond the scope of the initial attack campaign.
Affected Systems and Products
Note: The Affected systems and products account for all referenced vulnerabilities (CVE-2025-20333, CVE-2025-20363, CVE-2025-20362). For information mapping each vulnerability to a specific set of impacted versions, please see the Fixed Releases table in Cisco’s official Cisco Event Response documentation.
Mitigations and Workarounds
There are no workarounds or mitigations for these vulnerabilities. Organizations with Cisco ASA or FTD devices with VPN capabilities enabled should immediately apply the patches described above and following the “Detection Guidance” in this advisory to investigate for potential signs of adversary implants.
If systems cannot be immediately patched it is recommended that organizations take the following steps to reduce (but not eliminate) potential risks:
- Restrict access to VPN web interfaces allowing only trusted networks or IP addresses.
- VPN Portals should NOT be directly exposed to the internet only these patches are applied
- Disable unnecessary web services until patches can be applied
- Look for any signs of suspicious activity or compromise in forensic logs leveraging the “Detection Guidance” section of this document
Organizations with devices running the affected versions should review and follow the “Detection Guidance” section of this document.
Patches
Cisco has released patches for affected product families. Please reference the versions in the affected systems and product table above for specific versioning information to identify impacted products.
Patches are made available by Cisco via their Cisco Software Download Center
Technical Details
CISA has released an emergency directive publicly (ED 25-03) stating that it is tracking an active exploitation campaign targeting Cisco ASA and FirePower devices that leverage zero-day vulnerabilities to achieve unauthenticated remote code execution and post exploitation steps that manipulate the devices ROM for persistence. CISAs directive links this activity to the 2024 campaign Cisco calls “ArcaneDoor” and lists CVE-2025-20333 and CVE-2025-20362 among the CVEs being chained together in this attack.
Cisco’s related event response document states that ArcaneDoor was a campaign observed in early 2024, and assesses with “high confidence” the recent activity is related to the same threat actor. The actor was observed using advanced evasion techniques to prevent detection and analysis, including CLI command interception and disabling logging.
Weeks before Cisco released response materials to this incident, GreyNoise observed and reported on two significant scanning surges in late August that targeted Cisco ASA login portals and other related IOS services, with the first spike showing over 25,000 unique IPs and a large subset of that source traffic attributed to Brazilian botnet cluster. GreyNoise also noted that similar scanning spikes have in past cases preceded public CVE disclosures which could align with the information now provided by Cisco and CISA above.
Although the available pieces of activity from CISA, Cisco, and GreyNoise do not definitely state or publish a chain of evidence between the three public sources of information, the facts when placed together are consistent with a pattern where reconnaissance activity was followed by the disclosure of advisories and observed 0day exploitation in threat actor campaigns.
RELATED 0-DAY VULNERABILITIES
CISA’s KEV entry states that a missing authorization issue (CVE-2025-20362) can be chained with a WebVPN buffer-overflow condition (CVE-2025-20333) meaning that an attacker who first abuses the authorization flaw to reach restricted endpoints may then trigger a buffer overflow Remote Code Execution (RCE), potentially without needing valid credentials depending on device configuration. Cisco’s event response reporting corroborates this attack pattern, saying evidence “strongly indicates that CVE-2025-20333 and CVE 2025-20362 were used by attackers” in some cases to gain full control of vulnerable ASA and FTD devices.
CVE-2025-20363 is a broader web services remote code execution flaw reported at the same time, which allows unauthenticated remote attackers the ability to achieve remote code execution on unpatched devices. Within all the reported vulnerabilities in this advisory, risk is concentrated on VPN and HTTP/HTTPS web servers due to the improper handling of HTTP(S) requests.
A breakdown the recently disclosed vulnerabilities is provided below:
- CVE-2025-20333 – A flaw in Cisco’s ASA VPN web server, or WebVPN could allow authenticated attackers to perform remote code execution on affected devices. Cisco’s summary states that this is possible due to improper validation of user provided input within HTTPS requests to the service. If a device is vulnerable, a remote attacker with valid VPN user credentials can send malicious HTTP requests when the VPN web server is accessible, resulting in a buffer overflow condition and potentially achieve code execution as root. Cisco’s advisory also states that they’re aware of exploitation attempts for CVE-2025-20333, and that the vulnerability was found during resolution of a Cisco support case.
- CVE-2025-20362 – A vulnerability in Cisco’s ASA and Firewall Threat Defense (FTD) software allows an unauthenticated attacker to access restricted URL endpoints on these devices without appropriate authentication steps. The flaw exists due to lack of validation for user-supplied input in HTTPs requests. When the VPN web server is reachable, an attacker can send specific HTTP requests to web servers to access otherwise restricted URLs without authentication.
- CVE-2025-20363 – A flaw in Cisco’s ASA and Secure Firewall Threat Defense (FTD) IOS software could allow both unauthenticated and authenticated attackers the ability to perform remote code execution on affected devices due to improper validation of input in HTTP requests to vulnerable web services. If a remote attacker can gain access to exposed web services on a vulnerable device, they could execute code as root without authentication.
POST EXPLOITATION ACTIVITY
Cisco and CISA reports describe that in some observed incidents, the threat actor deployed custom implants on compromised devices to obtain persistence and remote control. Cisco’s event response writeup describes a threat actor capability where implants were constructed by modifying appliance low-level boot loader firmware, ROMMON, which enabled persistence on devices surviving reboots and other software upgrades. Cisco states this specific modification was only observed on some Cisco ASA 5500-X platforms as they were released before Secure Boot technologies were integrated into future product lines.
The U.K. NCSC also provided in depth reporting and malware analysis which details the low-level device boot process capabilities. The report names the persistent GRUB-based bootkit “RayInitiator”, which was observed being flashed to Cisco ASA 5500-X devices as a mechanism to survive reboots and firmware upgrades. The multi-stage bootkit was also used to load an x64 shellcode loader dubbed “LINE VIPER”. NCSC’s analysis of LINE VIPER showed that it was a shellcode loader that was used for executing CLI commands, capturing network packets, bypassing AAA, suppressing logging, forcing delayed reboots, harvesting victim CLI input, privilege escalation, and used as a mechanism to exfiltrate data.
NCSC’s report indicated that LINE VIPER accepted tasking and C2 communications using two actor-controlled channels. The first channel is described as a stealth WebVPN based method, using the appliances WebVPN and specially crafted HTTP requests to stage tasks, such as running a command or returning data. The secondary channel was reportedly observed using ICMP and TCP packets, where ICMP echo requests were sent containing tasking payloads. The two methods made C2 stealthy and offered resiliency.
The report contains additional detection guidance for identifying LINE VIPER or RayInitiator and can be found here. NCSC further states in the report that the specifically targeted ASAs are close to or past end of life, lacking Secure Boot which enabled the bootkit technique. Beazley Security strongly urges organizations with end of life appliance to replace them with supported products with more modern security features.
Other post exploitation activity includes executing commands on the device to suppress forensic syslog output from compromised devices and extending access to move laterally into victim environments.
Beazley Security Labs (BSL) strongly recommends that affected Cisco customers immediately apply vendor fixes as a primary measure to prevent this attack.
Organizations who had impacted devices publicly accessible via the internet, Beazley Security strongly recommends that such devices be investigated for integrity or other indicators of attack, and forensic artifacts be collected and searched. Detection Guidance has been provided by Beazley Security Labs below.
Detection Guidance
Both Cisco and CISA are closely tracking the specific attack campaign leveraging these previously unknown vulnerabilities. This campaign has been attributed to threat actors that carried out a previous campaign named “ArcaneDoor”, and Cisco clients may contact the Cisco Technical Assistance Center (TAC) with the keyword “ArcaneDoor” for information and guidance directly from the vendor.
CISA and Cisco have both published findings, Cisco has released this detailed report and accompanying detection guidance, while CISA’s guidance can be found in their supplemental ED 25-03 report. We have condensed and categorized some of the information here.
Please note that this threat actor has deployed many anti-forensics and anti-analysis measures including bootkits and in-memory modifications to Cisco IOS CLI commands, so all documented behaviors should be read and well understood before analyzing a device.
T1562.001 Impair Defenses: Disable or Modify Tools
Threat actors for this campaign have been observed suppressing specific syslog IDs related to network activity (302013, 302014,609002, and 710005). If logging for those events was previously enabled, then a noticeable reduction or absence of them may indicate malicious activity.
This threat actor has also targeted the checkheaps utility on Cisco devices. This utility normally runs every minute by default, and this can be verified with the command show checkheaps. Sample output from that command was provided in Cisco’s detection guidance:
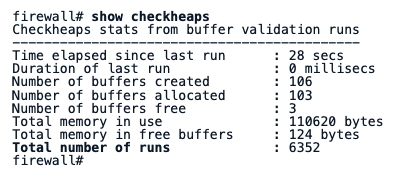
If the output of successive executions of that command do not show increases in “Total number of runs”, that may be an indicator of malicious activity.
CISA has also noted in their supplemental advisory that this threat actor has been observed hooking “tab” autocomplete functionality to crash an appliance, and that functionality should be avoided during investigation.
The LINE VIPER malware (observed on Cisco 5500-X series devices without Secure Boot) has been shown to perform modifications that impair forensic collection and detection of compromise. Techniques include rebooting devices before core dumps could be performed and tampering with copy commands to reboot the device when attempts to copy an image from the device were detected.
LINE VIPER also intercepts the verify command to return an expected firmware hash further hiding altered firmware. Unexpected or frequent reboots correlated with attempts to collect memory or copy firmware on these devices may be an indicator that the appliance may be compromised. If implants are confirmed, the device should be reimaged or replaced with a supported product.
T1078 Valid Accounts
This attack campaign is making use of stolen credentials to connect to the VPN. If a review of VPN logins reveals successful connections to accounts from geolocated IPs that are inconsistent with the internal user’s real physical location, that may indicate malicious activity.
T1542.003/004 Bootkit and ROMMON Manipulation
Reporting from Cisco, CISA, and the NCSC have detailed usage of bootkits and/or ROMMON abuse by threat actors in this campaign. CISA provided the following command to check for the presence of an implant:
more /binary system:/text | grep 55534154 41554156 41575756 488bb3a0
Any output from that command is an indicator of compromise.
Once an organization upgrades an affected appliance to a fixed version, users should check disk0: for the presence of a file named firmware_update.log. The presence of that file is an indicator of compromise, and users should contact the Cisco TAC with the output of the show tech-support command and the contents of the firmware_update.log file.
How Beazley Security is Responding
Beazley Security is monitoring client perimeter devices through our Karma product to identify impacted devices and support organizations in remediation of any issues found.
We are also conducting threat hunts across our MDR environment to detect potential exploitation attempts against our clients.
If you believe your organization may have been impacted by this attack campaign and need support, please contact our Incident Response team
Sources
- CISA: ED 25-03: Identify and Mitigate Potential Compromise of Cisco Devices
- Cisco Event Response: Continued Attacks Against Cisco Firewalls
- Cisco: Detection Guide for Continued Attacks against Cisco Firewalls by the Threat Actor behind ArcaneDoor
- Cisco Advisory cisco-sa-http-code-exec-WmfP3h3O (CVE-2025-20363)
- Cisco Advisory cisco-sa-asaftd-webvpn-z5xP8EUB (CVE-2025-20333)
- https://software.cisco.com/download/home
- Cisco Advisory cisco-sa-asaftd-webvpn-YROOTUW (CVE-2025-20362)
- https://www.greynoise.io/blog/scanning-surge-cisco-asa-devices
- https://www.cisa.gov/news-events/directives/supplemental-direction-ed-25-03-core-dump-and-hunt-instructions
Aware of an incident impacting your industry? Let us know:

