Critical Vulnerabilities in React and Next.js (React2Shell)
Executive Summary
12/12/25 Update: Two additional vulnerabilities affecting React have been disclosed that could allow an attacker the ability to create a denial-of-service condition within React functions and, in certain conditions, force a vulnerable server to leak potentially sensitive server functions and information (such as hard coded credentials). These newly identified vulnerabilities once again affect applications using React Server Components (RSC).
Originally issued fixes for React2Shell DO NOT address the below vulnerabilities. Additional risks identified include:
- CVE-2025-55183: An information leak vulnerability in React Server Components (RSC) after the original React2Shell fix. A flaw in RSC could allow attackers to remotely leak server-side source code of server functions, potentially exposing proprietary or sensitive information from the application without any authentication. Any secrets hard coded within source code may be exposed as part of this attack.
- CVE-2025-55184 & CVE-2025-67779 (impacting different minor versions): A React Function DoS vulnerability in React was discovered which was not mitigated by the original React2Shell fix. A flaw was discovered in RSC that could allow an unauthenticated attacker to send a malicious HTTP request to a Server Function endpoint and cause the server to become unresponsive. If successfully triggered, the affected application may be put into an infinite loop and stop processing requests, resulting in a denial-of-service condition.
Although React states the new vulnerabilities do not allow remote code execution, organizations utilizing RSC based solutions should ensure the follow-up patches are applied. Relevant sections of this advisory have been updated to provide additional details on these newly disclosed flaws.
12/05/25 Update: Soon after the React2shell vulnerability was made public, proof-of-concept exploits were published. The POC from the researcher who originally found the bug (Lachlan Davidson) can be found on his github. Reports of active exploitation by threat actors spread rapidly once the POCs were released.
On December 3rd, open-source web software library React disclosed a critical vulnerability in the React Server Components (RSC) “Flight” protocol impacting the React 19 ecosystem and frameworks that implement it, most notably Next.js. CVE-2025-55182 (React) and CVE-2025-66478 (Next.js) identify an insecure deserialization bug that can result in unauthenticated remote code execution (RCE) on the web server running node. The bug, found and reported by a security researcher, is present in default configurations of the affected software, so a standard deployment is immediately at risk without any custom hardening or configuration. React and Next.js are widely used across the internet and therefore this vulnerability requires immediate action.
Due to the high severity, apparent ease of exploitation, prevalence of the affected software, and active exploitation in the wild, Beazley Security recommends organizations prioritize immediate patching.
Affected Systems and Products
Patches
Important Update 12/12/2025: Original patches released to mitigate React2Shell (CVE-2025-55182) are still vulnerable to denial of service and source code exposure attacks. To address recently disclosed vulnerabilities CVE-2025-55183 and CVE-2025-55184, React have released new versions 19.0.3, 19.1.4, and 19.2.3. Additional upgrade information for the new vulnerabilities can be found within this React advisory.
Upgrading to patched versions of the software is the only definitive mitigation for CVE-2025-55182, CVE-2025-66478, CVE-2025-55183, and CVE-2025-55184. To remediate, update React 19.0/19.1/19.2 to 19.0.3 / 19.1.4 / 19.2.3 respectively. EOL 18.x releases should upgrade to major supported versions and patch in order to mitigate all vulnerabilities. Update Next.js (App Router) to a patched release in your version line: 14.3.0-canary.88, 15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7, or 16.0.7. More information on the original React2Shell vulnerability can be found in the React advisory.
Technical Details
12/12/2025 Update: Following the earlier React2shell disclosure, researchers have identified additional flaws within React Server Components (RSC). Newly tracked vulnerabilities, CVE-2025-55183, CVE-2025-55184 and CVE-2025-67779, may allow malicious requests to result in unintended source code disclosure or denial of service under certain conditions respectively:
- CVE-2025-55183: An information leak vulnerability in React Server Components (RSC) after the original React2Shell fix. A flaw in RSC could allow attackers to remotely leak server-side source code of server functions, potentially exposing proprietary or sensitive information from the application without any authentication. Any secrets hard coded within source code may be exposed as part of this attack.
- CVE-2025-55184 & CVE-2025-67779 (impacting different minor versions): A React Function DoS vulnerability in React was discovered which was not mitigated by the original React2Shell fix. A flaw was discovered in RSC that could allow an unauthenticated attacker to send a malicious HTTP request to a Server Function endpoint and cause the server to become unresponsive. If successfully triggered, the affected application may be put into an infinite loop and stop processing requests, resulting in a denial-of-service condition.
The core vulnerability reported (CVE-2025-55182) was found in a React Server Component (RSC) called the “Flight” protocol. RSCs are interesting in that, unlike most web software which runs on client browsers, RSCs run on web servers. That means this vulnerability will be present on an organization’s network edge, meaning threat actors can abuse it to gain initial access.
In-depth technical details were not provided by either the discovering researcher or the React organization. However, the “Flight” protocol is a network serialization library, and the vulnerability was reported to be a deserialization bug. Deserialization is a system process where two remote software systems can transmit and share data objects over the network. The process involves encoding an in-memory object into a stream of bytes that can be sent over a network (serialization), then reversing the process on the receiving end (deserialization). If this is not done in a secure way, malicious data can be injected directly to code. Third party cybersecurity company Wiz reported that they have successfully exploited the bug in their testing but have not released technical details or proof-of-concept code.
Soon after the vulnerability was publicly reported, POCs started to emerge on the internet. The researcher who originally discovered the bug (Lachlan Davidson) published his POCs on his github. There was an additional POC published by security researcher Moritz Sanft, who included some more in-depth analysis of the software bug.
According to a walkthrough of the vulnerability on Sanft’s POC, the root issue is that the deserialization done by the React Flight system does not adequately check object parameters that can be passed by unauthenticated requests. This allows an attacker to leverage a prototype pollution vulnerability to inject arbitrary commands that will be executed on a target web server when it processes a maliciously crafted request. A brief explanation of the mechanics of the bug can be illustrated using Lachlan’s POC payload shown below:
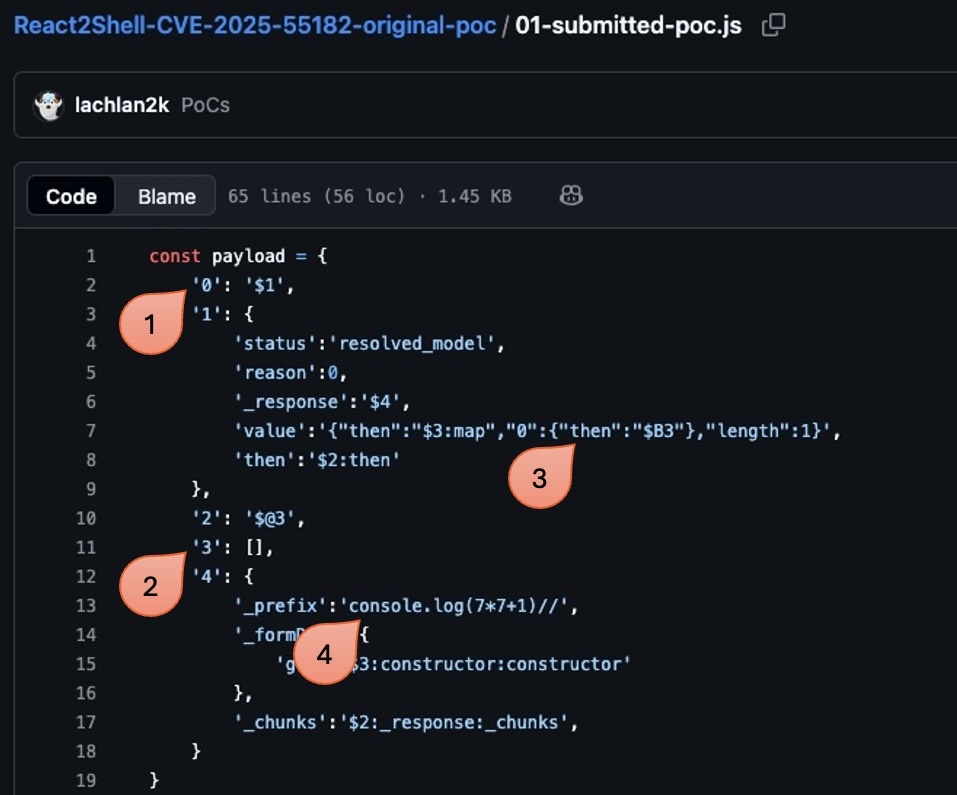
1. The React Flight protocol utilizes json objects pictured above and refers to them internally as “Chunks”
2. JavaScript provides a lot of freedom, and attack code can directly reference Chunk object structure
3. This allows an attacker to overwrite internal structures (in this case the internal Chunk .then() function)
4. And inject arbitrary code that will be executed by the web server process
In the above example, it will simply calculate the expression ‘7*7+1’ and output it to console, but other organizations have started to see threat actors leveraging JavaScript server objects that can execute processes on the server. The following payload was reported by Jacob Baines at VulnCheck:
"_prefix": "var res=process.mainModule.require('child_process').execSync('ping -x 1<x.x.x.x>',{'timeout':8000}.toString().trim();; ...
How Beazley Security is Responding
Beazley Security is monitoring client perimeter devices through our Exposure Management Platform to identify impacted devices andsupport organizations in remediation of any issues found.
We are also conducting threat hunts across our MDR environment to detect potential exploitation attempts against our clients.
If you believe your organization may have been impacted by this attack campaign and need support, please contact our Incident Response team.
Sources
- Wiz: Critical Vulnerabilities in React and Next.js: everything you need to know
- React.dev: Critical Security Vulnerability in React Server Components
- Vercel: Summary of CVE-2025-55182
- NIST: CVE-2025-55182
- GitHub:React2Shell-CVE-2025-55182-original-poc
- Datadog:CVE-2025-55182 (React2Shell): Remote code execution in React Server Components and Next.js
Aware of an incident impacting your industry? Let us know:

